AsiaTechDaily – Asia's Leading Tech and Startup Media Platform

Why do we still need to invest in Email Security Enhancement?
Emails most vulnerable link for cyber security threats
Emails are the weak link in cyber security as over 90 percent of malware is initiated through mailing systems, even for enterprises deploying multiple security solutions to protect their infrastructure.
Malware, phishing and URL-based threats all exploit emails as a valuable vector for cyber attacks and the recent threat faced by Chosun Media Group is a testament to such threats.
According to Media Today, on August 18, 2021, Chosun Ilbo said a hacking attempt was made by a professional hacker’s group targeting the emails used by the Chosun Media Group employees.
Following the incident, the company asked its employees to be careful while opening their emails. Employees of Chosun Media Group said that on August 5, they received an email with the subject line, “I am Eun-Yeol Choi, a student from Hong Kong.”
However, when the PDF file attached to this email was opened, a malicious code got installed on all the employees’ computers.
In its newsletter, the Chosun said, “Fortunately, the Digital Chosun CTS system team in charge of online security for Chosun Media Group immediately identified this fact and responded promptly to prevent a malicious code infection. We ask you to be extra careful about the security of the online environment and follow compliance.”
The Chosun Ilbo also stated that this case is quite similar to the North Korean hacking style because there was a previous case involving the JoongAng Ilbo website. During the time, the involvement of North Korean hackers was suspected.
The grand old newspaper agency believes that this hack seems to have exploited a vulnerability in a PDF file that has been modified in the technique of planting malicious codes in popular MS Word or Hangul documents.
Since the hack, the Chosun Ilbo administration has issued an advisory instructing their employees to refrain from opening an email with a warning sign.
The advisory suggests that emails with files from unknown sources should be deleted immediately.
Suppose any abnormal symptoms occur in the PC after checking the email or executing the attached file. In that case, employees should immediately contact the Digital Chosun CTS system team to receive security instructions.
The importance of the email security solution
Most advanced threats use emails to deliver URLs linked to phishing sites or download malicious programs and weaponized file attachments by applying malicious codes in document (non-PE) files.
As emails are highly targeted and increase the odds of exploitation from cyber-attacks, organizations must ensure that their email security solution protects them from advanced cyber threats.
ChaSung Lim, the founder and CEO of SecuLetter said, “As corporate security has been strengthened, it has become difficult for malicious codes to penetrate inside easily. However, unlike exe executable files, which mail service providers can easily block, it is difficult to block all document files as they may be necessary for work, so malicious code penetration using document files is actively taking place.”
Things to do for an email security solution
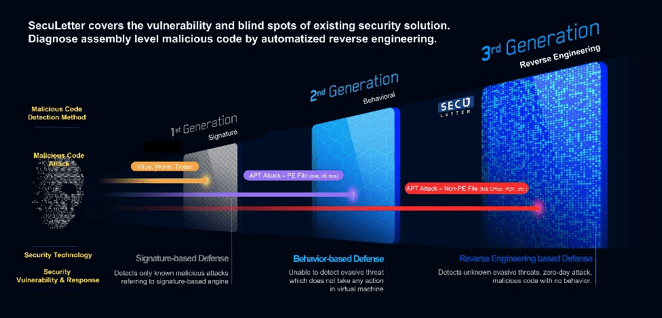
Until most recently, signature-based solutions such as antivirus and antispam have been the mainstay of malware detection. However, the increasing number of targeted attacks often do not have signatures because they create new malicious codes.
To make up for the weak points, behavior-based detection solutions such as sandboxes have also appeared. Still, there are ways to bypass them, such as evasion of virtual environments and time-lag attacks, and loopholes in malware detection have also begun to appear.
In particular, unlike executable files that are blocked directly by the mail server, it is more difficult to detect malicious codes included in images or document files.
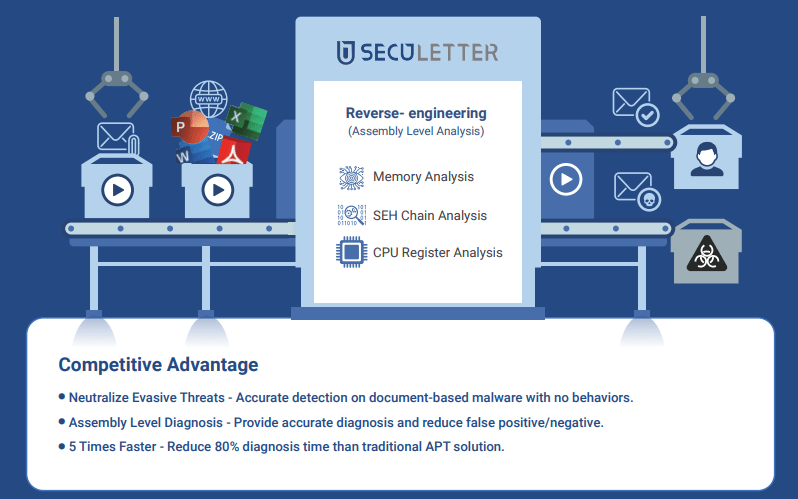
Because of that, SecuLetter emphasizes that malicious code in non-executable files such as document files can be detected by reverse engineering analysis.
Malicious code analysts use technology to diagnose malware at the assembly level and find sophisticated attack attempts that signature/behavioral-based detection solutions cannot.
SecuLetter is based on the ‘MARS (Malware Analysis Reverse-engineering System)’ engine that analyzes non-executable files at the assembly level to find malicious behaviors is supplied.
Besides the advanced email security solution, it is also critical that email users are required special attention when opening emails from suspicious senders or handling document files.