AsiaTechDaily – Asia's Leading Tech and Startup Media Platform

Removal of non-executable file malware using assembly-level reverse engineering
Scrutinizing the number of malicious codes included in emails gathered from a company, which has 4,000 employees, using a signature-based security detection solution was able to detect only eight codes after removing duplicate files for a month, while SecuLetter’s dynamic detection technology was processing, the number of malicious codes found was 40. It poses a huge question mark over security if a company fails to fathom that it was infected with 40 malicious codes instead of 8 exposing it to newer cyber security threats.
Chasung, Lim, CEO of SecuLetter, said, “Most companies realize that it is infected with malicious codes only after hacker announces the attack. In other cases, the news of the attack comes from an external organization.”
At the ’20th Next-Generation Security Vision 2021′ summit on the 26th October, CEO Chasung, Lim exposed the limitations of existing signature and behavior-based solutions through a session under the theme of ‘Cyber prevention for the digital age, respond with new technology.’
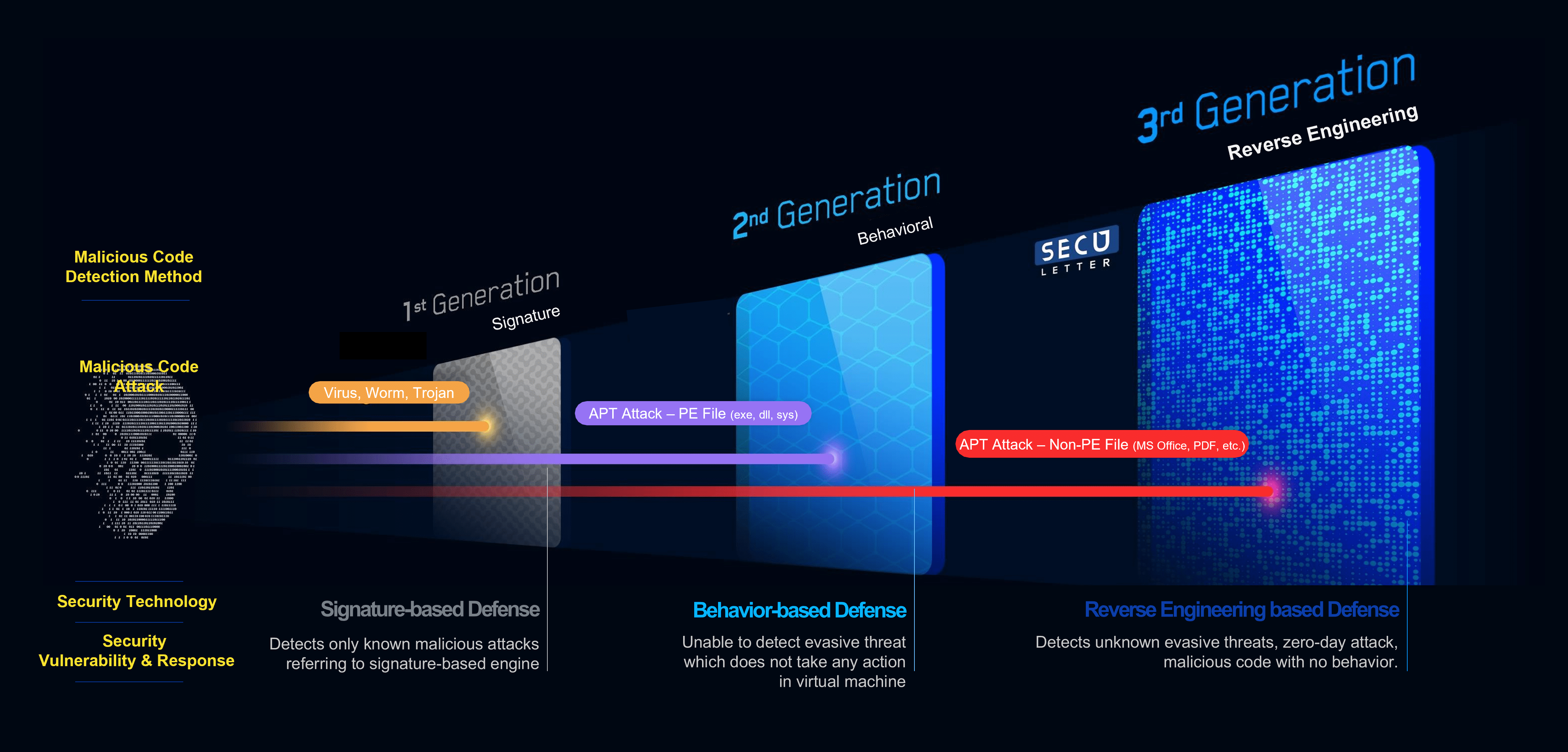
He said, “After the attack starts, the attacker has infinite possibilities based on which they conduct an attack. It is much safer to fundamentally block the attack before the action of attack starts, at a stage where there are few actions that hackers can do within the normal flow. The attacker does not directly introduce malicious code in the form of an executable file but causes malicious behavior by using normal functions and processes in non-executable files,” said Chasung, Lim. He explained that the SecuLetter MARS engine could accurately find abnormal behavior in a typical process by analyzing it at the assembly level.
In 43seconds analysis of unknown threats
SecuLetter focuses on non-executable files such as documents since most of the malicious codes in the form of executable files are currently blocked before internal network access. In a network separation environment or corporate mail security policy and webmail, EXE attachments are blocked by default. Although there is a method to change the extension to make it look like a document file, it is also cut off and not able to reach out to users.
Attacks using non-executable files cannot be blocked solely either by signature-based security solutions or sandbox behavior-based solutions. These security solutions are designed to identify specific malwares so that they fail to launch if the malware does not perform a malicious function programmed to recognize. In the sandbox, the solution executes the file waiting for 5 to 20 minutes to check if any malicious activity is occurring. But, if the malicious action is programmed to trigger 3 hours after the file has been executed, the sandbox fails to detect this threat. Imagine the inconvenience caused by a user waiting for five minutes each time the transmission takes place.
Chasung, Lim said,“SecuLetter analyzes the assembly level of non-executable files, and the threat analysis is completed within 43 seconds. SecuLetter is the Next-generation APT solution that completes analysis in less than a minute.”
Implementation of cyber-attack prevention through CDR or reverse engineering
Cyber-attacks with non-executable files are of two types. The first one uses the normal functions of the document wherein macros, and JavaScript inserted, which is required to open it. As soon as the document is opened, the macros are executed and the malicious behavior occurs. To prevent this type attacks, the defense mechanism is called CDR (Content Disarm and Reconstruction). It is a computer security technology for removing potentially malicious code from files. Unlike malware analysis, CDR technology removes all file components within the system’s definitions and policies.
The second type of attack exploits the vulnerabilities in specific document editing applications, specific fonts, tables, etc. In these types of attacks, malicious actions are executed automatically even before the user can take any actions. If a CDR defense mechanism eliminates these vulnerabilities, it must remove all attributes and edits from the document and create a new text file. In such cases, it becomes impossible to proceed with the work normally and CDR may fail to eliminate it.
However, SecuLetter Next-generation APT solution uses both CDR and reverse engineering to eliminate attacks implemented by using non-executable files. It can be supplied as a built-in solution, and cyber prevention can be conveniently carried out using the cloud.
CEO Lim said, “It is important to educate employees to be careful about attacks and make it habit by the simulation attack training, but it is fundamentally critical to block any potential misuse in an attack. It is more effective to cut it off.” he said.
References with proven technology leadership
SecuLetter’s excellent technology has already been proven through the success stories of several companies and public institutions. BNK(Busan Bank) created an APT attack defense system with the SecuLetter solution. It has tremendous effect in defending against the latest intelligent attacks using non-executable files.
As many financial institutions have made network connection guidelines mandatory to prepare for detection unknown malicious codes, it is expected to adopt the solution in various places. There is no problem with the security system even at home or remote work environment by providing almost real-time analysis and detection with accuracy.